The First Step Toward Security Rule Compliance Is
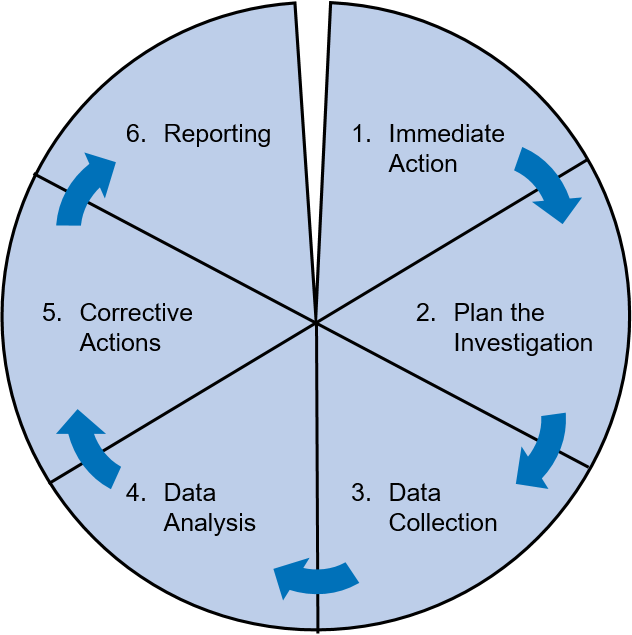
Six Steps For Successful Incident Investigation Risktec


Network Segmentation Solution Algosec

A Global Regulatory Sandbox Collaboration Policies And Solutions For Cross Border Compliance Compliance Sandbox Regulatory Compliance Emerging Technology

Threat Modeling Technical Walkthrough And Tutorial Infosec Resources
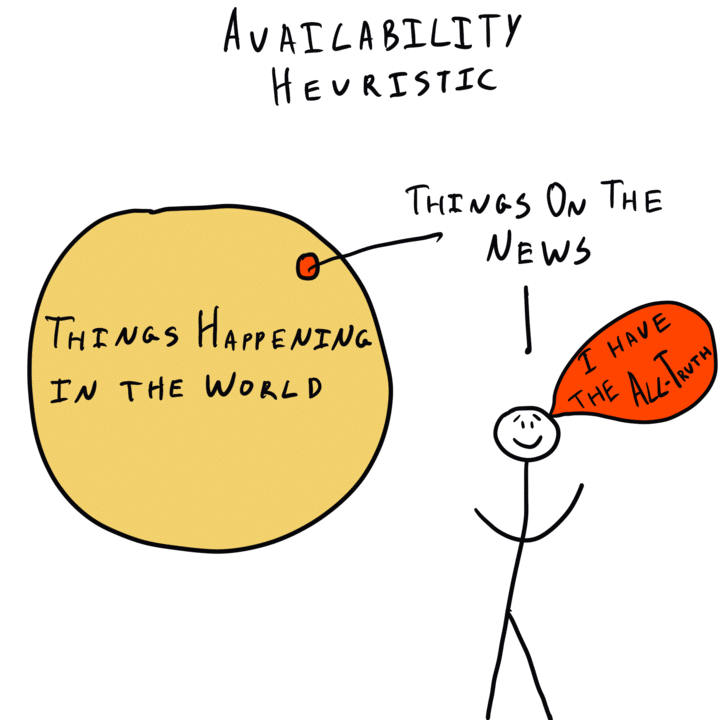
Availability Heuristic The Decision Lab

Vulnerable Software List Software Cyber Security Threats Antivirus Program

What Is Consent Management Platform And Why You Need It Data Privacy Manager
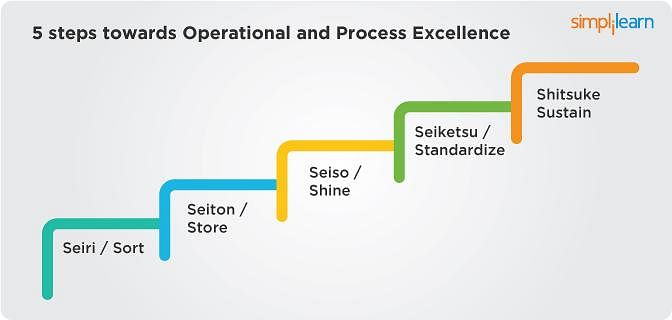
Implementing 5s Methodology The First Step Toward Workplace Efficiency Updated
Github Enterprise Onboarding Guide Github Resources

What Is Consent Management Platform And Why You Need It Data Privacy Manager

Robotic Process Automation Rpa Using Uipath Automation Information Technology Services Robotic Automation

Being Cautious Is One Of The Steps Towards Safety Have A Safe Sunday Today Safety Quotes Safety Message Safety

Implementing 5s Methodology The First Step Toward Workplace Efficiency Updated
3 Interoperability Layers Joinup

Advanced Registration Forms Fusionauth

Advanced Registration Forms Fusionauth

How We Developed The Ibm Security Gdpr Framework Data Security Development Framework

